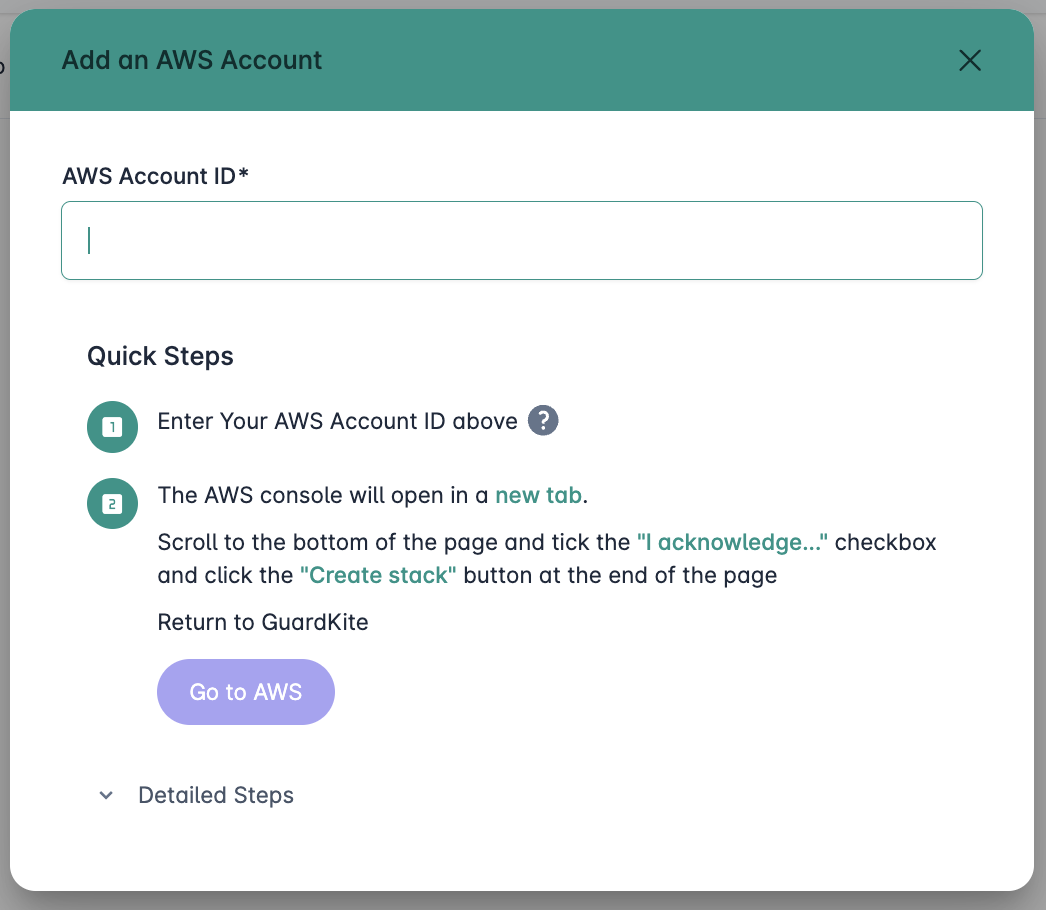
Step 1 - Link your AWS Account
GuardKite works by scanning your AWS resources for security and compliance issues using a secure, read-only IAM role. To enable scanning, you need to link your AWS account by deploying a CloudFormation stack that creates the required IAM role with minimal permissions.
👉 GuardKite only requires read-only access to your AWS account. It does not modify, delete, or create any resources. For a detailed breakdown of the IAM policies used, visit the IAM Role Permissions page.
To register with GuardKite, go to app.guardkite.com and click Sign Up. Use the Google button or enter your email address to create an account.
Step-by-Step Guide
You must be logged into your AWS account that you want to link to GuardKite.
1. Enter Your AWS Account ID
When you log in to GuardKite for the first time, you will be directed to the Add an AWS Account wizard.
- Enter your 12-digit AWS Account ID in the provided field.
- Click the Go to AWS button. This will open the AWS CloudFormation console in a new tab.
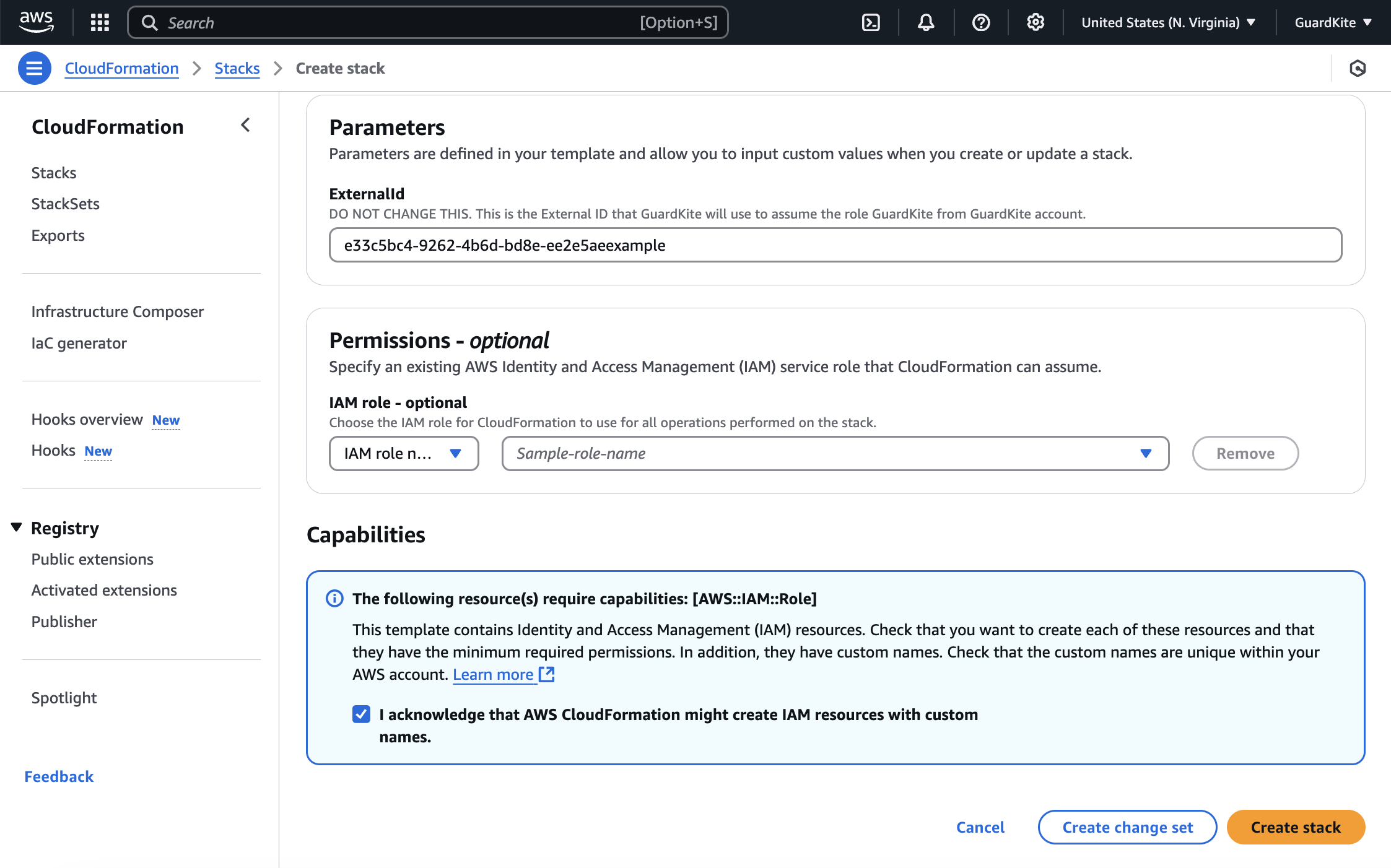
2. Deploy the GuardKite CloudFormation Stack
- In the CloudFormation console:
- Select the Capabilities checkbox.
- Click Create Stack.
- Wait for the stack creation to complete. The status should change to CREATE_COMPLETE.
- Return to GuardKite.
3. Initial Scan
Once the CloudFormation stack is successfully created, GuardKite will start scanning your AWS resources.
The initial scan will take upto 5 minutes to complete and you will receive an email notification once the scan is finished.
To learn more about the scan results and how to interpret them, visit the Findings) page.
Advanced Deployment (Optional)
If you prefer to deploy the GuardKite CloudFormation template manually, you can:
- Download the CloudFormation template by expanding Detailed steps in the wizard.
- Review the template and deploy it in the AWS CloudFormation console.
- Use the provided External ID when setting up the IAM role.